The online world is increasingly becoming more and more data driven. Organizations collect and save a huge amount of personal data (PD) of customers or Personally Identifiable Information (PII) on their systems which they might analyze and use to send further marketing mails, information about new products etc.
GDPR, CCPA, CPRA, HIPAA, COPPA, GLBA, PIPEDA, POPIA, and other data privacy laws regulate how PD and PII are collected, stored, how data subjects are informed, and what the data subject can do in order to get this information deleted from the company systems. Organizations have to comply with these stringent data privacy regulations and ensure that the data has proper administrative safeguards, and access controls to ensure that it remains confidential.
Further, organizations also have to process data deletion requests from data owners for deletion of their PII data from the organizations IT systems. As such, organizations need to keep a track of all the PII information on their systems and have a proper mechanism to deal with requests for deletion of such data and remove all traces of the personal data as requested. Failure to adhere to data privacy regulations might lead to fines, lengthy lawsuits, and even a ban on business operations in certain jurisdictions.
Why Seqrite Data Privacy?
Using Seqrite Data Privacy, you can carry out the following activities to comply with the stringent data privacy regulations:
- View the spread of customer PD/PII on enterprise data systems spread across the globe.
- Tag, sort, and classify such information as required.
- Track the data under various domains such as healthcare, Financial, Government or Personal.
- Track data by compliance regulations such as GDPR, CCPA, CPRA, HIPAA, COPPA, GLBA, PIPEDA, POPIA, and others.
- Configure data sources and securely connect to these data sources and search for PII information.
- Search and perform a deep scan on all configured data sources for any PII data.
- Track, locate, and delete PII information on receiving requests.
- View, process, and track workflow for customer data subject requests for deletion.
Additionally, Seqrite Data Privacy also compliments and collaborates with other Seqrite products such as Seqrite Centralized Security Management, Seqrite XDR, to give a complete one point solution for organization data security. Seqrite Data Privacy can be deployed in multiple configurations (Cloud/In-premise/Partly both).
Seqrite Data Privacy Variants
Seqrite Data Privacy comes in different variants: Standard and Enterprise.
- Standard: Standard Seqrite Data Privacy has minimum required features.
- Enterprise: Enterprise Seqrite Data Privacy has comprehensive features to effectively search, scan, locate, classify, and delete data for received requests.
Getting Started With Basics
Before we get started, let us go through some of the basic terms and concepts on which Seqrite Data Privacy functionality is based.
Personally Identifiable Information (PII)
Your organization may solicit customers for its products, services, or applications in a variety of ways using online or offline methods. In either of these channels, when a customer avails your products, services or applications, they may be required to enter some personal details into some online application form or offline. This data is saved in the organization’s computer databases for various applications.
The PII data could be of the following types or more:
- Name
- Email address
- Credit/Debit Card details
- Social Security Number
- PAN card number
- Driving License number
- Address
Data Subject Request (DSR)
A customer who may have availed your organization services, websites, or products, would have entered some PII information on your websites or applications. In light of data privacy regulations enacted worldwide, the customer may after some time request your organization to delete this PII from the records permanently.
To get this done, the customer may send a Data Subject Request (DSR) to get his PII data deleted from the company records. The customer may use the service request portal or send an email request to the designated email address to get that done.
Data Sources
Data Sources are the databases, file systems, messaging applications behind the actual applications that hold the customer data. These data sources hold the customer PII data. There can be multiple databases across geographically different locations.
Currently, Seqrite Data Privacy supports the following types of databases:
- Mongo
- Mysql
- AWS S3
- MS-SQL
- Oracle
- One Drive
- Manual action data sources
- MS teams
- Salesforce
- File servers
- Outlook 365
- Vision Helpdesk
Connectors
Connectors help Seqrite Data Privacy engine to connect to various data sources so that the databases can be scanned for any PD/PII data. Connectors are available for all known standard databases.
Classifiers
Classifiers help you define the PD/PII data types that are commonly used across the world.
You can use classifiers to identify PII information in the following sequence:
- The administrator configures data sources and instances.
- A deep scan is performed on the data sources using default and custom classifiers.
- Seqrite Data Privacy engine displays the classification results that further need to be verified.
- You can use the PII found in deep scan to search for records of a specific person.
This information is later used to delete the PII data from the databases based on the DSR.
Seqrite Data Privacy has a large number of default classifiers (100+) that you can use to classify PII. You can also create custom classifiers as required. Default classifiers cannot be deleted. However, you can copy them and modify them to create custom classifiers.
Tags
Tags help you categorize classifiers by compliance types, for example GDPR, CCPA, CPRA, HIPAA, COPPA, GLBA, PIPEDA, POPIA, etc. Tags also help you categorize classifiers by data sensitivity, data value, data impact etc. Default tags are pre-configured in Seqrite Data Privacy. You can create custom tags as required. Default tags cannot be deleted. However, you can copy them and modify them to create custom tags.
Workflow
To begin using Seqrite Data Privacy, you need to do the following:
- Configure users.
- Configure classifiers.
- Configure tags.
- Configure data sources/ instances.
- Perform deep scan, dashboard will be populated.
- View, verify classifiers list manually. Now the scan is completed.
- Search profiles based on the PII to be found.
- Create requests, process, assign requests to appropriate person.
- Search for personal data as per DSR.
- Carry out appropriate action and update request table.
- Inform end user who has raised DSR.
Prerequisites
The following prerequisites are required to set up your organization in Seqrite Data Privacy.
-
The customer AWS account must have a vCPU limit of 48.
To view the current vCPU limit for your AWS account, go to
https://console.aws.amazon.com/ec2/#Limits and search for ‘Running On-Demand All Standard’.
Creating an Azure client to access files from One Drive
To get files from One Drive, register the application on Azure Active Directory. To create an Azure client to access files from One Drive, follow these steps.
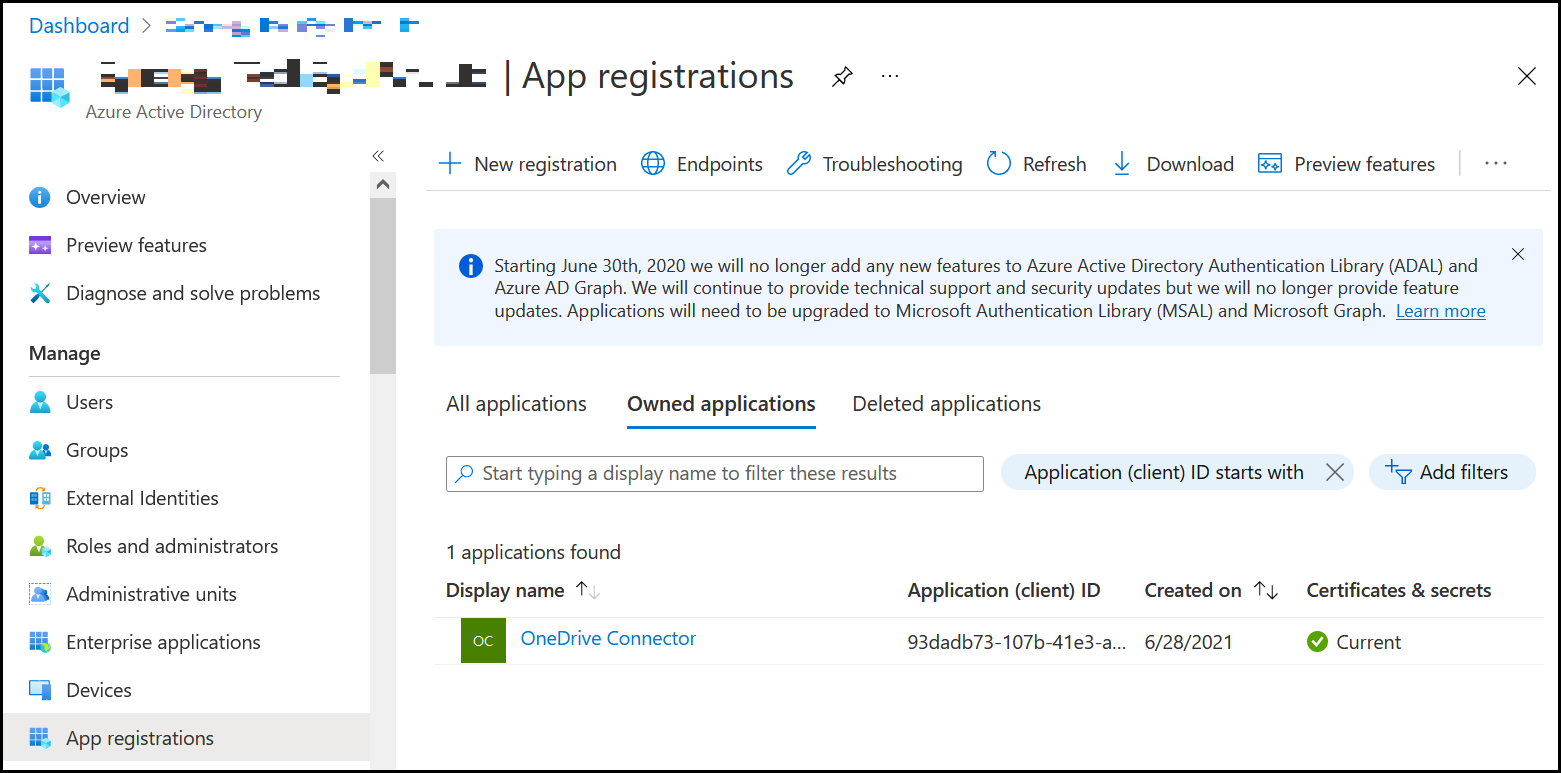
- Open a web browser. Navigate to the Azure Active Directory admin center and sign in using an organization admin account (Microsoft work account).
- Click Azure Active Directory in the left navigation pane. Then click App registrations under Manage.
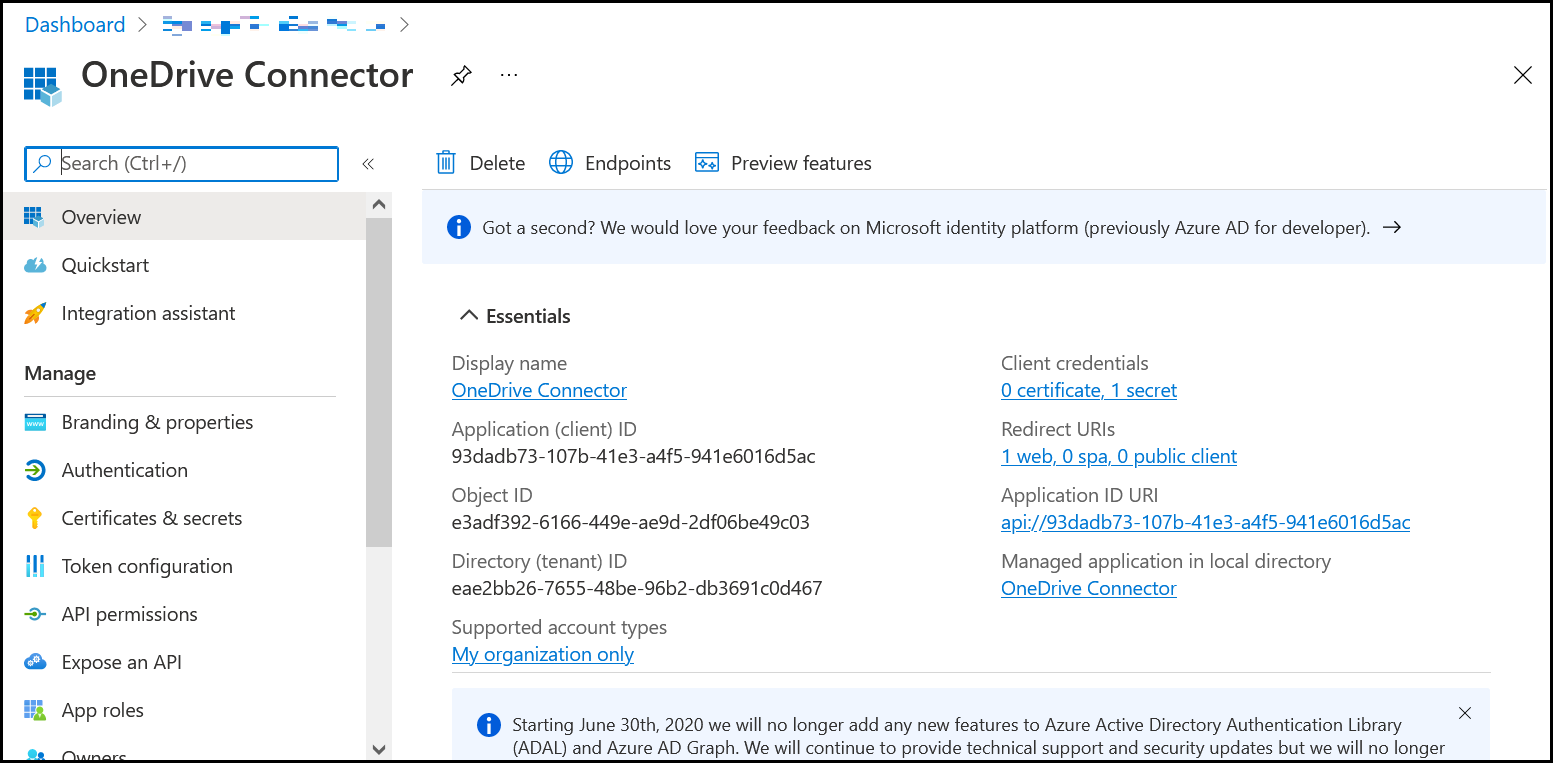
- Click New registration. On the Register an application page, enter the appropriate values. To know more, refer https://docs.microsoft.com/en-us/graph/tutorials/java?view=graph-rest-1.0&tutorial-step=2
- On the application overview page, copy the value of the Application (client) ID and save it on clipboard to use it in the next step.
-
Click Register.
-
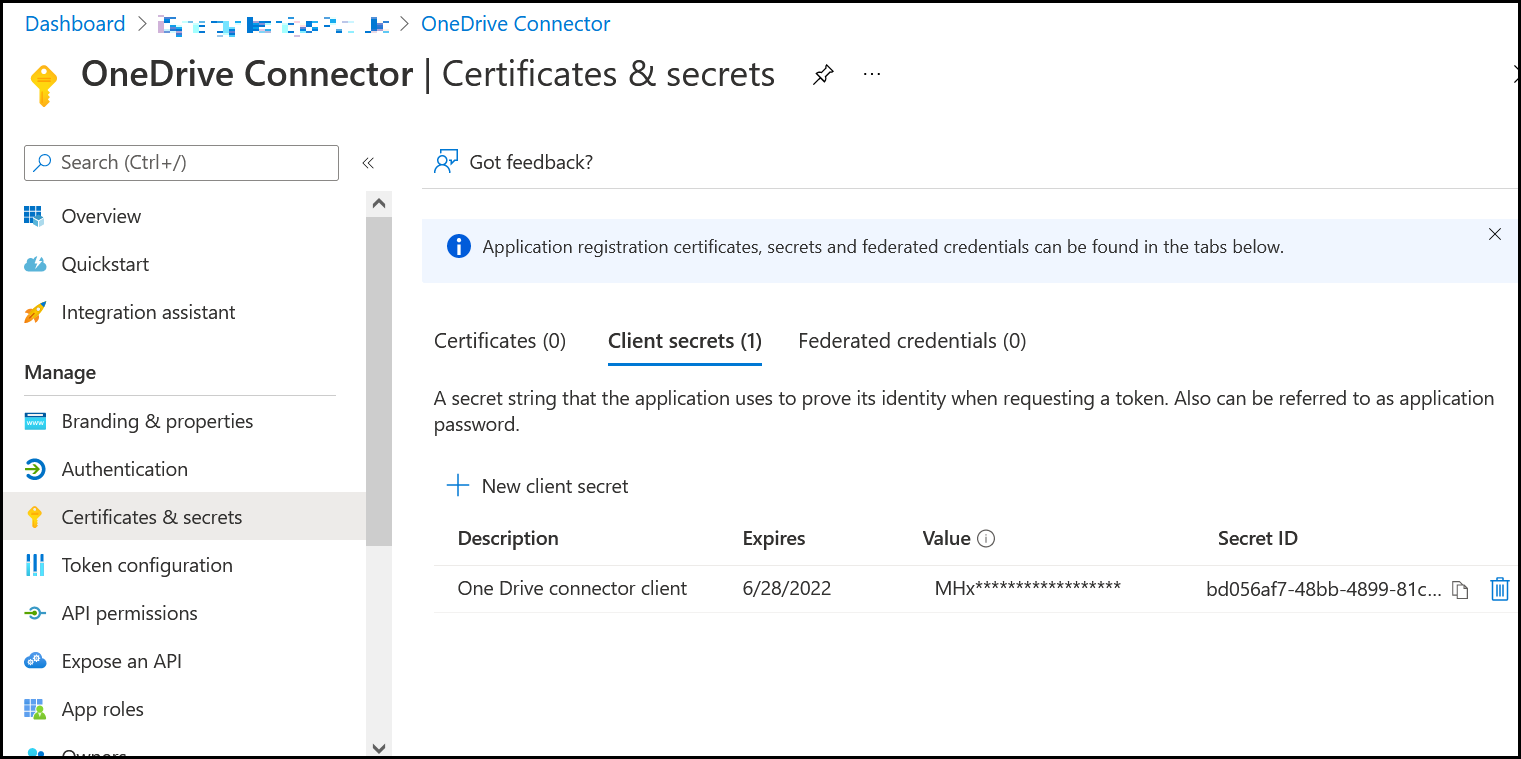
Navigate to Manage > Certificates and Secrets, then click New Client Secret.
-
Copy the client secret. Save it on clipboard to use it in the next step.
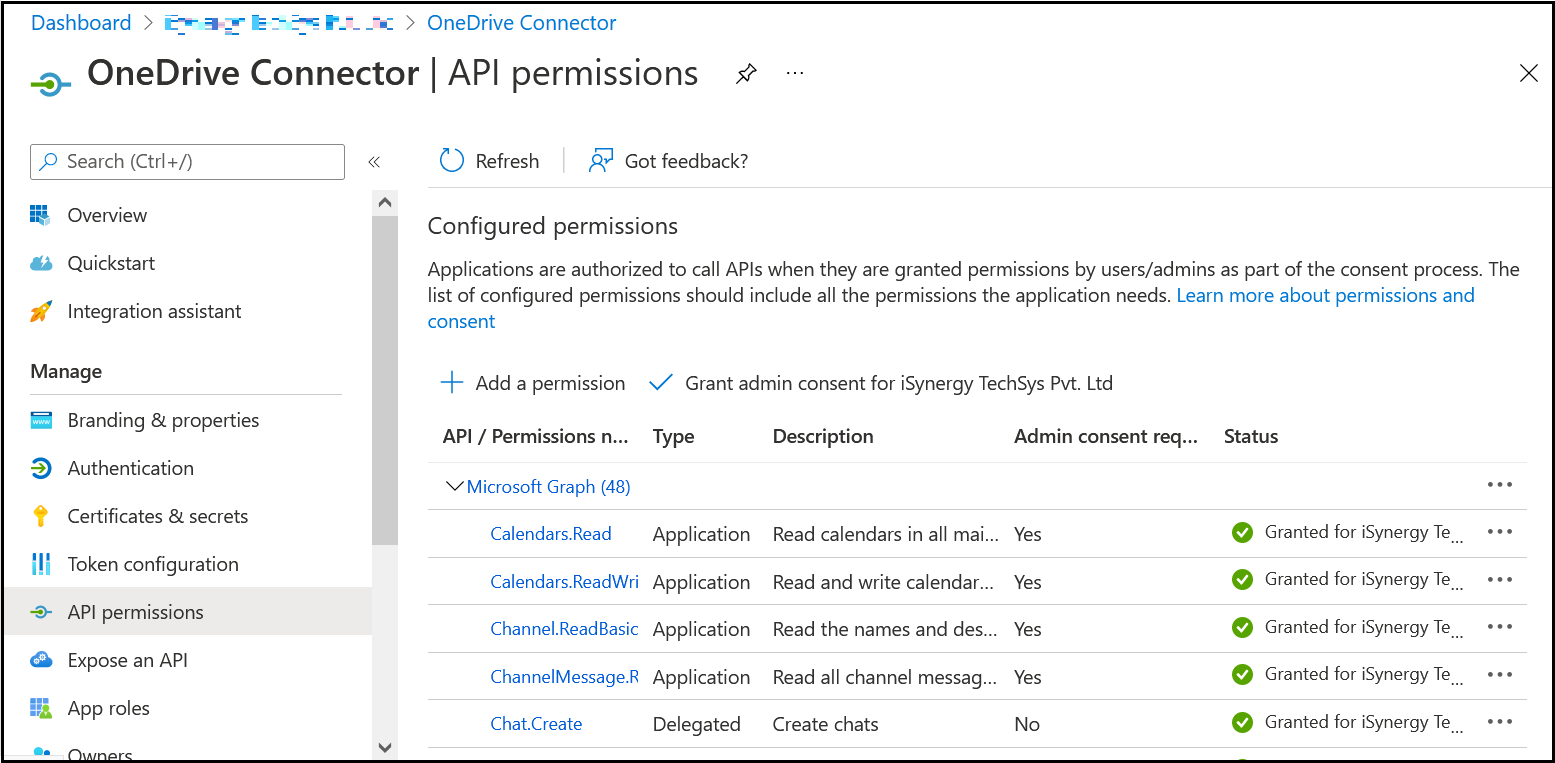
- Navigate to Manage > API Permission, then click Add a permission.
- Click Microsoft Graph, then click permission type (For more details, refer Entity. Select the required permissions.)
- Delegation Permissions: Your application needs to access the web API as the signed-in user, but with access limited by the selected permission. This type of permission can be granted by a user unless the permission is configured as requiring administrator consent.
- Application Permissions: Your application needs to access the web API directly as itself (no user context). This type of permission requires the administrator’s consent and is also not available for the native client applications.
- Application (client) ID is used for creating client.
- Directory (tenant) ID is used as tenant ID while creating client.
Authorities
Create client secret key to access API’s. Applications are authorized to call APIs when they are granted permissions by users/admins as part of the consent process. The list of configured permissions must include all the permissions needed by the application. To know more, refer
https://docs.microsoft.com/en-us/azure/active-directory/develop/v2-permissions-and-consent?WT.mc_id=Portal-Microsoft_AAD_RegisteredApps
Entity
System Requirements
Supported Web Browsers
The following Web browsers are supported for accessing Seqrite Data Privacy.
| Operating System | Supported Browsers |
|---|---|
| Windows | Google Chrome, Mozilla Firefox, Microsoft Edge |
| Linux | Google Chrome, Mozilla Firefox, Microsoft Edge |
| Mac | Google Chrome |

