In the present era, organizations allow their employees to bring smartphones, tablets, and handheld devices to the office and use the mobile devices for official tasks. In such scenario, it is important to monitor mobile devices to protect data of the organizations.
Seqrite mSuite console is a turnkey solution that empowers the organizations to remotely monitor, manage, and track all types of mobile devices to implement compliance polices on the digital devices and ensure that the corporate data are secure.
Advantages of Seqrite mSuite
Following are the advantages of Seqrite mSuite.
- Monitor the mobile devices if they comply with the policy of the organizations.
- Implement the required security on the mobile devices including Android and iOS devices.
- Secure the data of the organizations.
- Monitor resources to enhance productivity.
- Maintain instant communications with the employees.
- Perform console administration functions.
- Monitor network data usage and call/SMS.
- Manage device app with app configuration.
- Generate the customized reports.
- Remotely access the enrolled mobile device.
How does Seqrite mSuite work?
Seqrite mSuite works on the Agent-Server architecture where the console is hosted on Cloud to manage the mobile devices. The agents are installed on all the supported operating system of mobile platforms (Android, iOS). Seqrite mSuite Admin gets full control of the device to manage, monitor, or track the device.
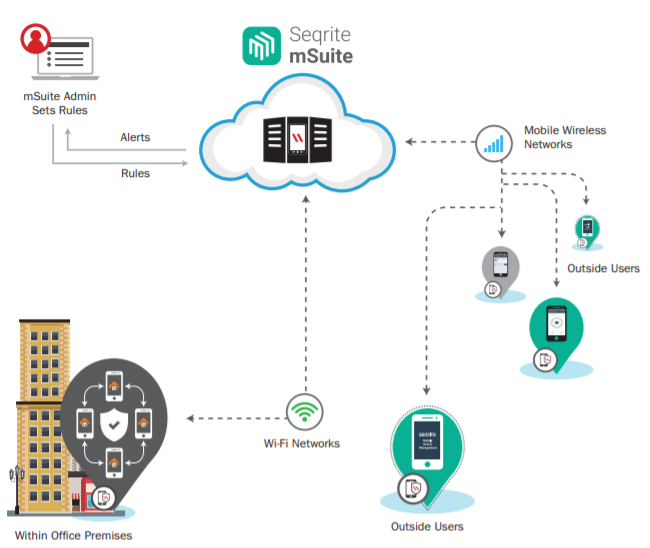
Seqrite mSuite allows the administrators to deploy and enroll Seqrite mSuite Agent on the mobile devices remotely, apply required policies and configurations such as App Configuration, Web Security Configuration, Anti-theft, Network Data usage, Fence Configuration and so on, on the mobile devices.
Seqrite mSuite Agent acts on the mobile devices silently and apply most of the restrictions without user intervention. Seqrite mSuite Agent has built-in antivirus that keeps the devices safe from any virus attack.
This chapter includes the following sections.

