Policies govern the connections that are attempted from users to applications. A policy prevents unauthorized users from accessing any applications. It also grants access to authorized users to access specific applications as required.
On this page, you can create policies for users and applications and publish them. If the policies are pushed to the gateway and successfully applied, the status is updated as published.
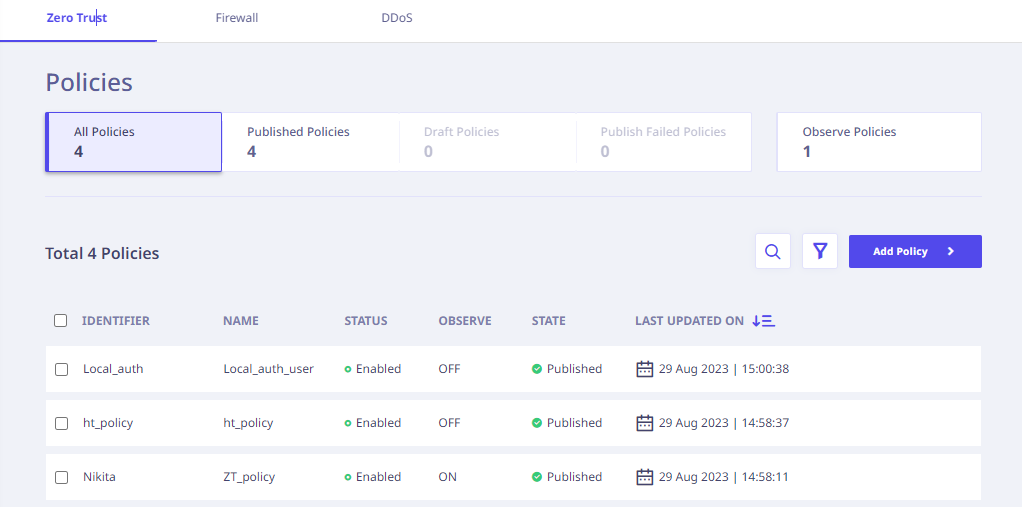
At the top of the page, few widgets display the count for All, Published, Draft, Publish Failed and Observe Policies.
Policy States
| Policy State | Description |
|---|---|
| Published | A policy that is successfully configured and allows a user to access applications accordingly is a Published Policy. |
| Draft | Administrator can create some policies that may not be implemented immediately or may be needed later. Such policies are saved as Draft Policies. |
| Publish failed | If a policy fails to be applied to a site, it is a Publish Failed policy. |
Observe
An administrator may want to monitor certain connection attempts. So, Administrator can create a policy with Observe mode on. This type of policy is an Observe policy.
Connections attempted under such policy will be allowed but will be represented with a different color on the Visibility page.
Further, the following details of all the existing policies are listed.
| Column Name | Description |
|---|---|
| IDENTIFIER | Suitable identifier for the policy. |
| NAME | Name of the policy. |
| STATUS | Current status of the policy. |
| OBSERVE | Denotes whether the connections allowed under the policy will be observed or not. |
| STATE | Current state of the policy. |
| LAST UPDATED ON | The date and time on which the policy was last updated. |
| WAF Configured | To enable WAF rules for the policies. |
| Search | To search policies by name. |
| Add Filter | To add a filter. To know more, refer the Adding a filter to refine the view section on Visibility page. |
| Refresh | Click the icon on the upper right corner to refresh the page. |
| Add Policy | Click the Add Policy icon in the upper right corner to add a policy. |
The policies can be sorted by name when you click the sorting symbol next to the NAME column.
Actions available with policies
When you hover over each policy, the following options appear on the right side next to the Last Updated On column.
| Action Icon | Action Label | Description |
|---|---|---|
 |
Edit | To edit the details of the policy. |
 |
Delete | To delete the policy. |
 |
View and Edit details | To view and edit the details of the policy. |
Click a policy to view policy details in the right pane.
| Fields | Description |
|---|---|
| Detailed Information | |
| Identifier | Policy Identifier. |
| Name | Policy Name. |
| Status | Current status of the policy. |
| Observe | Whether connection is being observed or not. |
| State | Current state of the policy. |
| Last Updated On | The date and time on which the policy was last updated on. |
| Last Updated by | The administrator who last updated the policy. |
| Description | Policy description. |
| IdP Name | The name of the identity provider. |
| Expiry Date | The expiry date of the policy. |
| Allow Rule | |
| User Tags | User Tags related to the policy. |
| Application Tags | Application Tags related to the policy. |
| Quick Actions | |
| Enable | A toggle button to enable the policy. |
| Observe | A toggle button to activate the ‘Observe’ flag, indicating whether the connection is being monitored or not. |
Adding a policy
Adding a Zero Trust Policy
To add a Zero Trust Policy, follow these steps.
- Click the Add Policy button. The Add Zero Trust Policy page appears.
-
Enter the following information in the Policy Information section.
- Enter the identifier for the policy.
- Enter the policy name.
- Select On or OFF under Observe.
This indicates whether the connections allowed under this policy are marked as Observed on Visibility page. - Enter the detailed description of the policy.
-
Enter the following information in the Allow Rule section.
- Select the any one of the local or external prominent identity providers.
- Enter the user tags.
These are the tags applied on user from where the connection is established. - Enter the application Tags.
These are the tags applied on applications where the connection is received. - Enter the user exception tags.
Based on connection requirement, these tags will exclude users to whom available source tags are applicable.Note:
The Application and User Tags are fetched from the Centralized Security Management Tags. Please refer
Centralized Security Management Tags for more details.
- Provide an expiry date found within the Timebound Access section. Once the expiration date reached, the policy will no longer be usable.
Note:☛
The administrator can select an expiration date extending up to 12 months, with the ability to renew the policy thereafter. - After entering this information, you can click Save as Draft or Add policy as required.
Adding a Firewall Policy
To add a firewall policy, follow these steps.
- Enter the identifier for the policy.
- Enter the policy name.
- The default mode is selected as Blocked by default.
- Select On or OFF under Observe.
This indicates whether the connections blocked under this policy are marked as Observed on Visibility page. - Enter the detailed description of the policy.
- Select the applications to which you want to apply the policy.
- Enter the Blocked IP list. You can add a single IP address or multiple IP addresses, or subnets as required. All these addresses must be separated by a comma.
- Enter the Allowed IP addresses/ list.
- Select the list of Blocked countries from where the connections are originating.
- Enter the common application parameters as required.
- After entering this information, you can click Save as Draft or Add policy as required.
Adding a DDoS Policy
To add a DDoS policy, follow these steps.
- Enter the identifier for the policy.
- Enter the policy name.
- Enter the detailed description of the policy.
- Select the applications to which you want to apply the policy.
- Select the Rate-Limiting Scope (whether the DDoS Rule should be applied on the basis of origin IP address or destination applications.) either IP Address or Application.
- Enter time in seconds for Time Frame for which the number of connections will be calculated.
- Enter the number of requests that will be allowed for the specified Time Frame. If the number of requests exceeds this number, then the connections will be blocked.
- Enter the allowed IP address list.
- Enter the common application parameters as required.
- After entering this information, you can click Save as Draft or Add policy as required.
Example 1
Adding a firewall policy for restricting a user
If you want to block traffic originating from a user with particular source IP address and country, follow these steps.
- Log on to Seqrite ZTNA portal. Navigate to Policy Management in the left pane.
- Click the Firewall tab at the top.
- Click the Add Policy button.
- Enter the identifier and name as required.
- Enter the source IP address as 35.123.23.21. You can enter more IP addresses or subnets if you wish to.
- Enter the exceptions IP addresses (Whitelisted IP Address), if any.
- Select the applications to which you want to apply the policy.
- From the list of countries, select China.
- From the common application parameters, select custom path.
- Add the value as admininfo.
- After this is done, click Add Policy.
After this policy is applied, a user with source IP 35.123.23.21 and source country China will not be able to access configured application with custom path /admininfo (eg: www.example.com/admininfo if example is the selected application).

