Creating a Gateway SAML app on google workspace
To configure a web application for Seqrite ZTNA user portal authentication on Google workspace admin console, follow these steps. This application is used for SAML authentication.
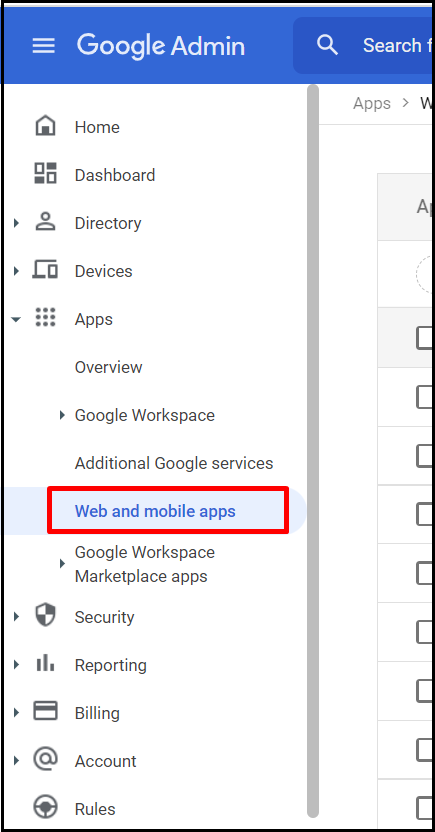
- Log on to your google workspace admin console and navigate to Apps > Web and mobile apps.
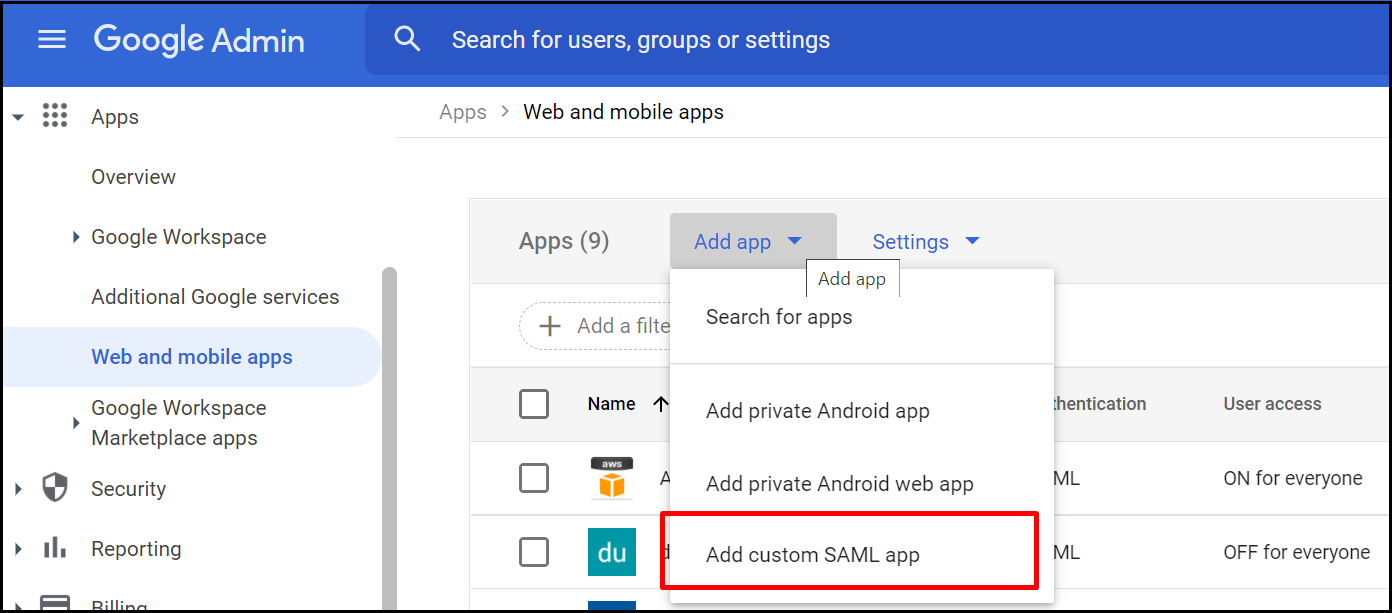
- Click the Add app drop-down menu and select Add custom SAML app.
- Provide your app details such as App name and Description and click Continue.
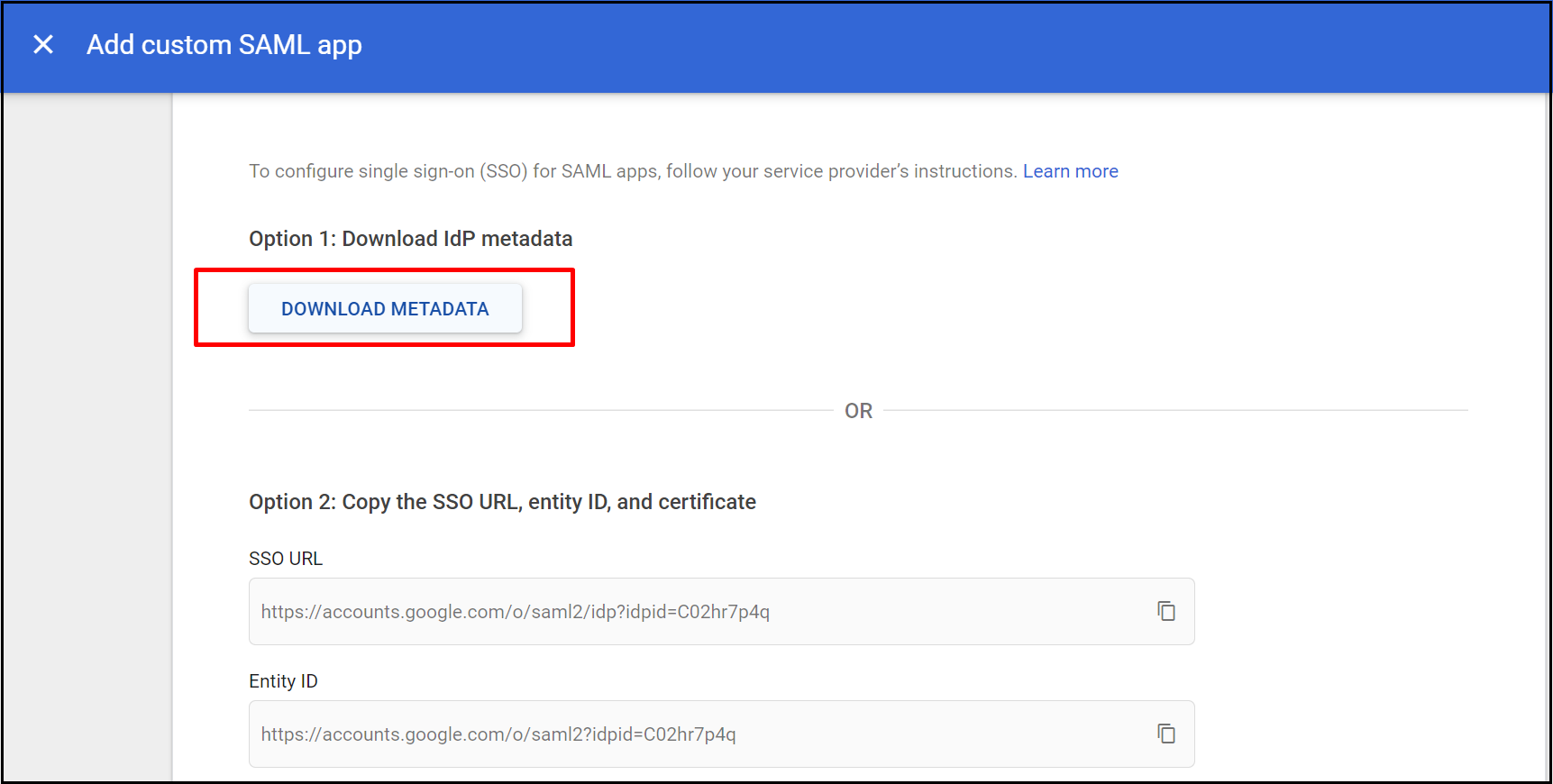
- Click Download Metadata to download the metadata xml file used to configure IDP while onboarding on the admin console. Click Continue.
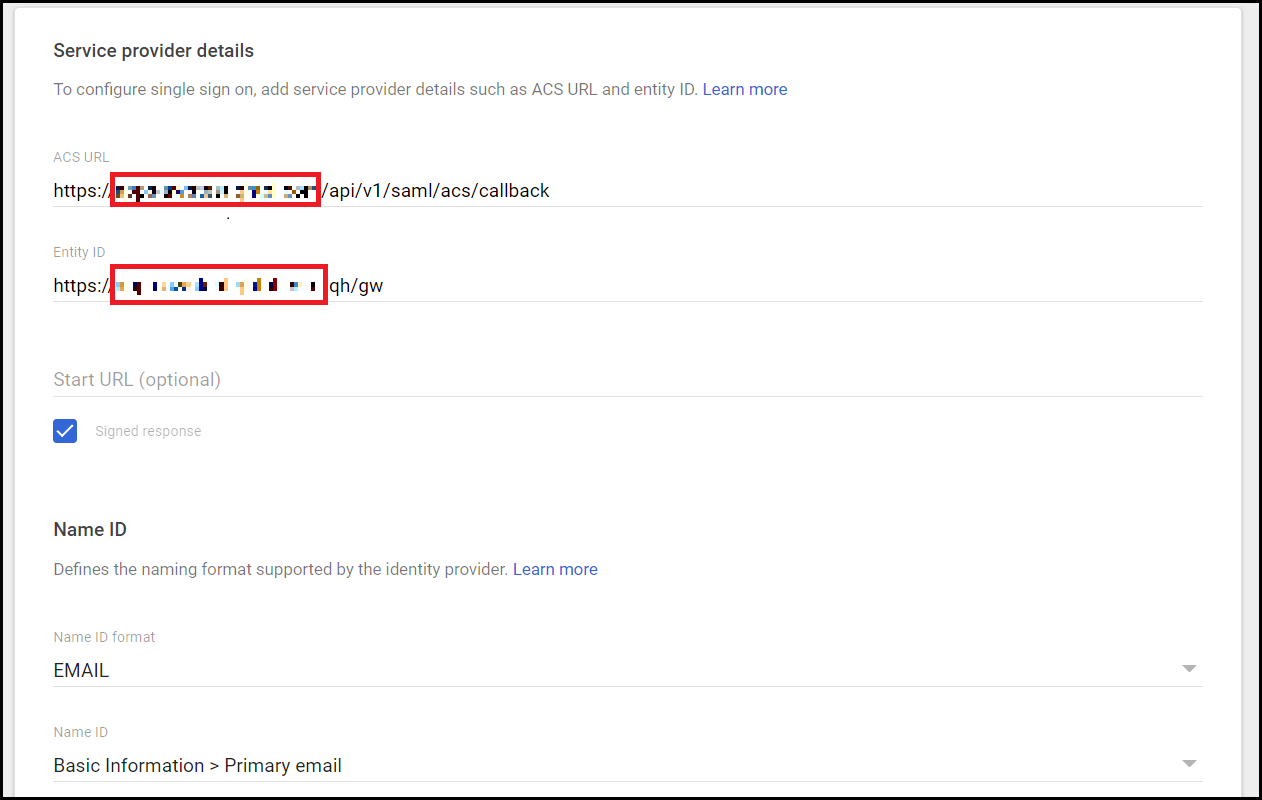
- On the Service provider details page, enter the following details.
- Enter the ACS URL.
- Enter the entity ID.
- Select the checkbox for signed response option.
- Select Email in Name ID format.
- In Name ID, select Basic Information> Email.
Note:
The ACS URL and the Entity ID must contain your company domain on which you want to host the Seqrite ZTNA Gateway.- Example ACS URL: https://company.com/api/v1/saml/acs/callback
- Example entity ID: https://company.com/qh/gw
- In this step, we have to add the mappings.
- In the basic information drop-down menu, select Primary email.
- Enter the attribute name.
- Click Add Mapping. Click Save.
Note:
The app attribute name should be in all lowercase alphabets only as used in the example ‘email’. Alphanumeric, special chars and space should not be used.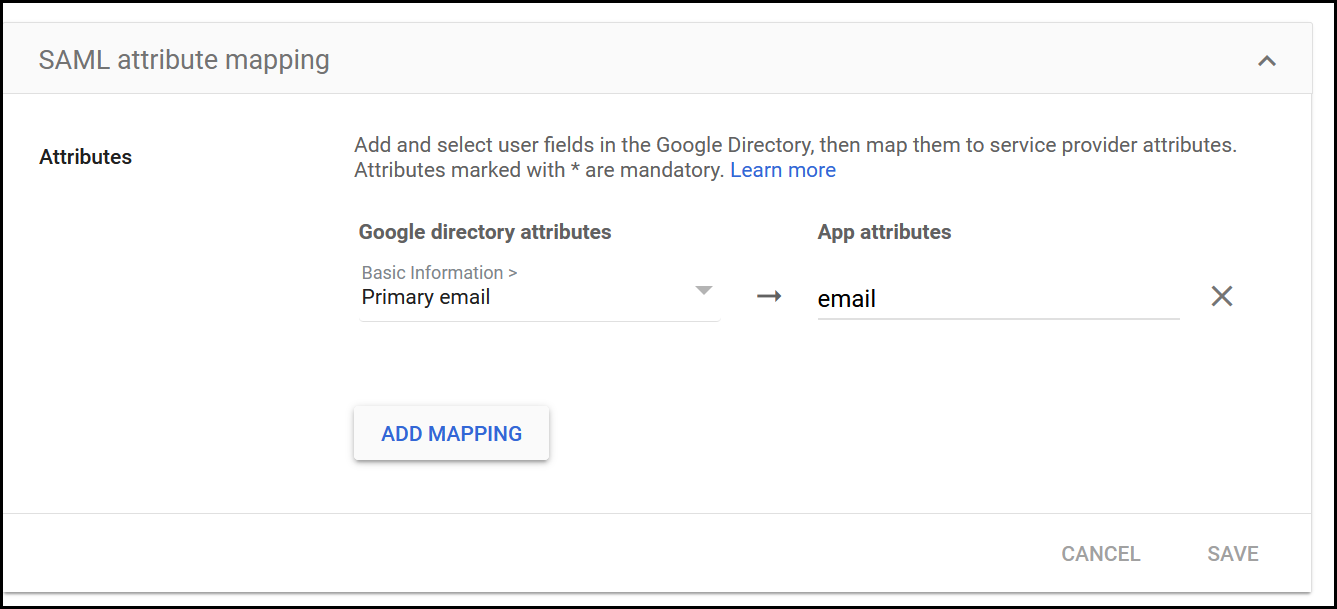
- After finishing the app creation, navigate to the created app.
Make sure the user access for this app is turned ON as highlighted in the following image.
If it is not turned on, click the View details button and select On.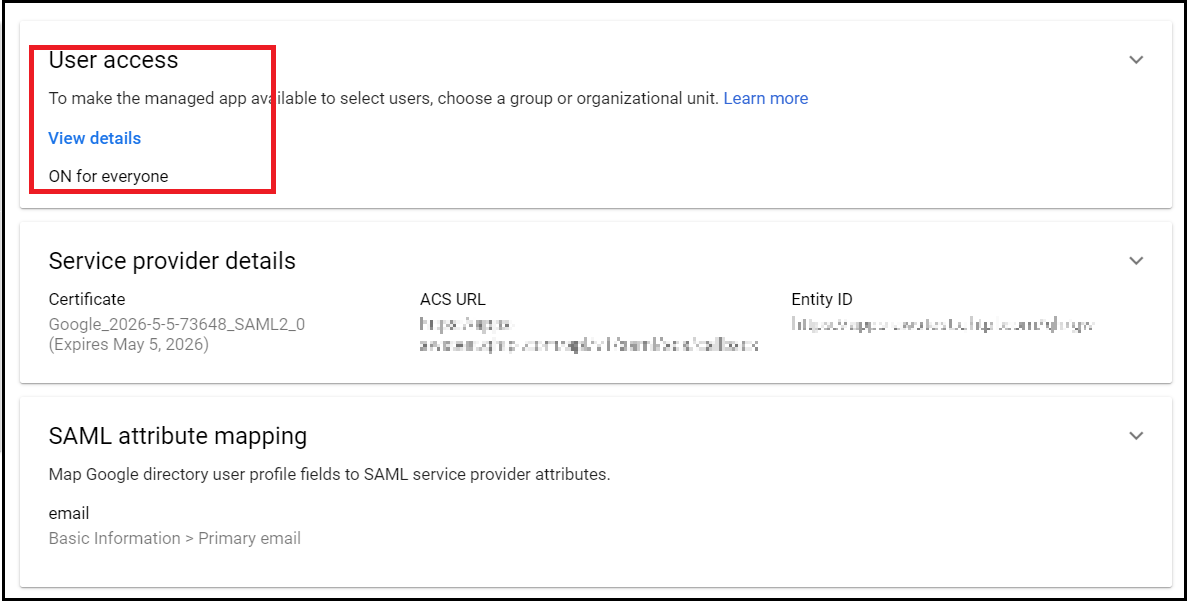
The SAML application is now ready to be used for authenticating the google workspace users on the Seqrite ZTNA user portal.
Creating a user sync app on google cloud console
- Log on to the Google Cloud Platform https://console.cloud.google.com/
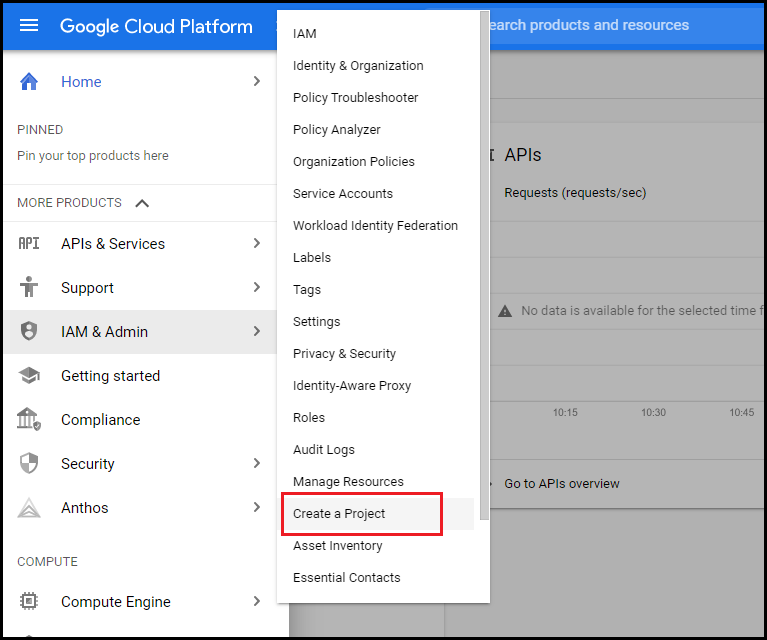
In the left pane, navigate to IAM & Services > Create a Project.
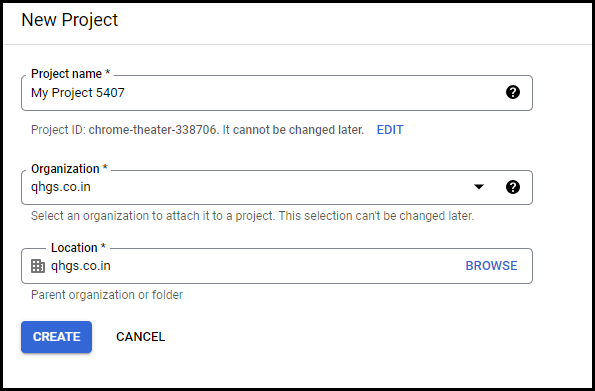
Fill all the required information and click Create.
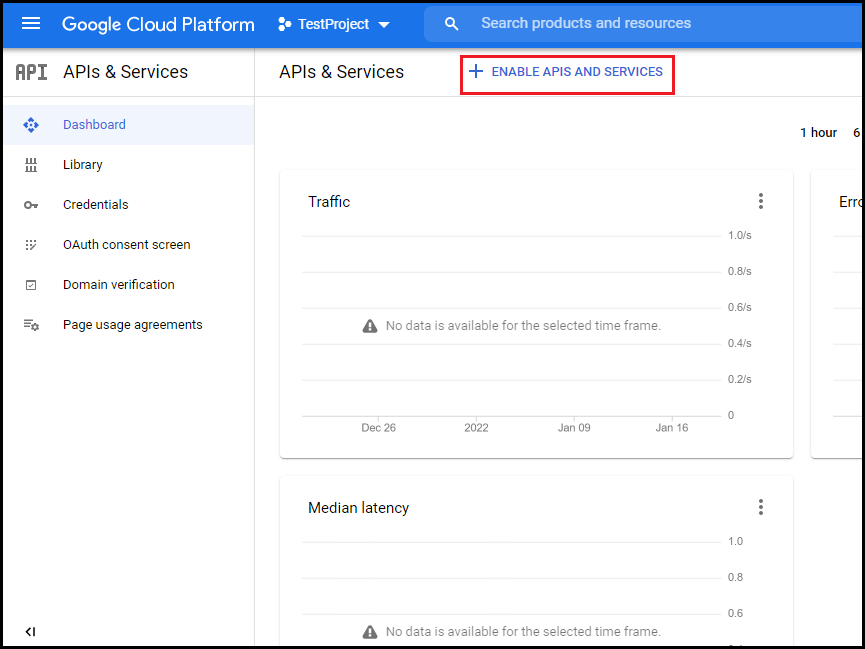
- In the left pane, navigate to APIs & Services > Dashboard.
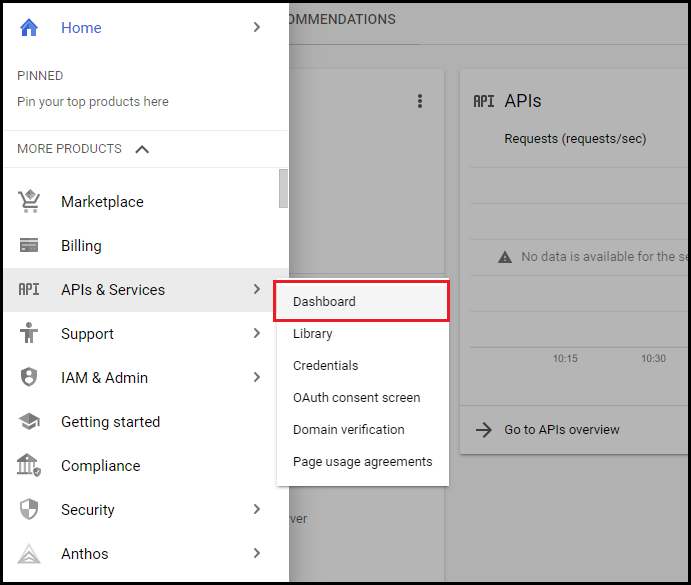
- Click ENABLE APIS AND SERVICES.
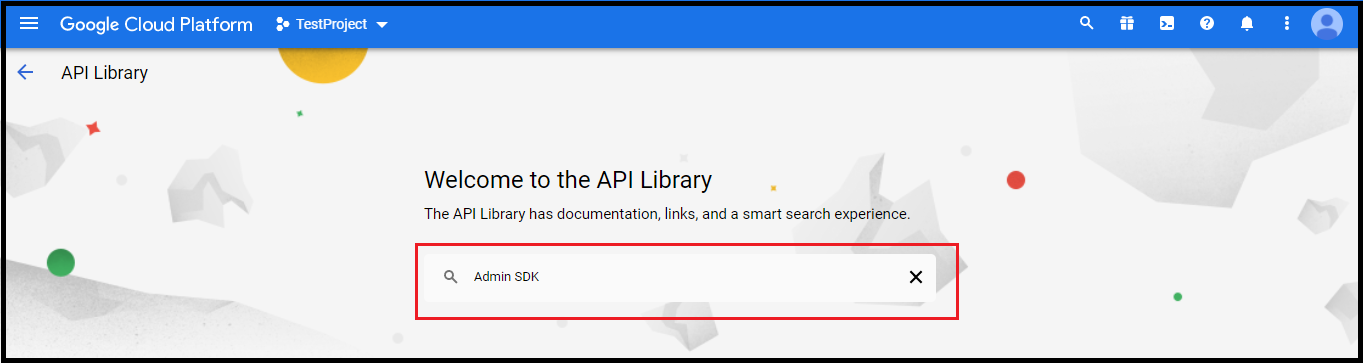
- In the API Library search box, search Admin SDK and select Admin SDK API.
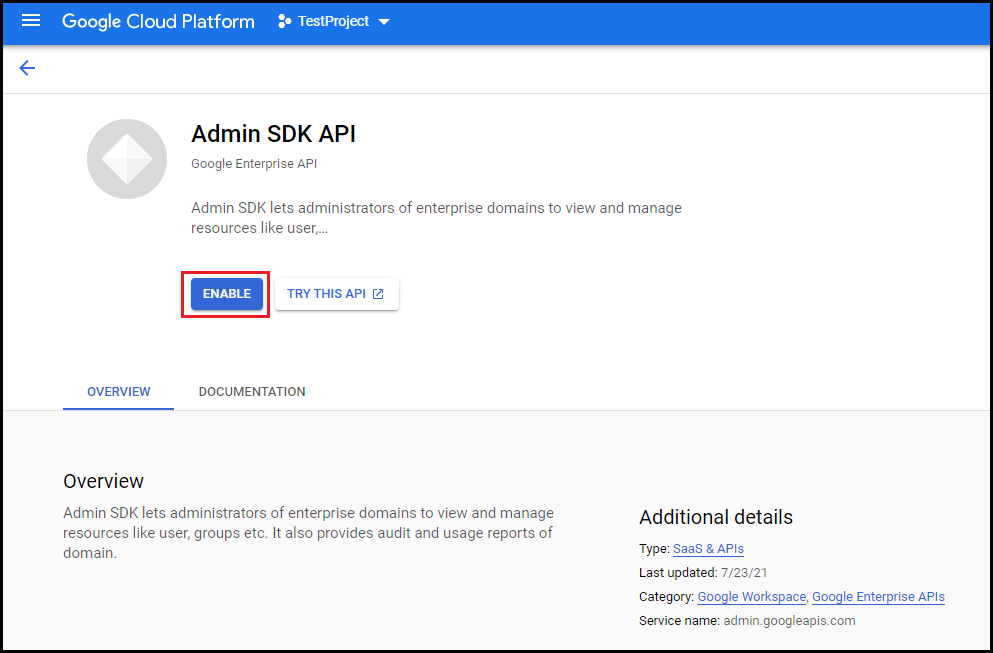
- Click the Enable button.
- In left pane, navigate to APIs & Services and select Credentials.
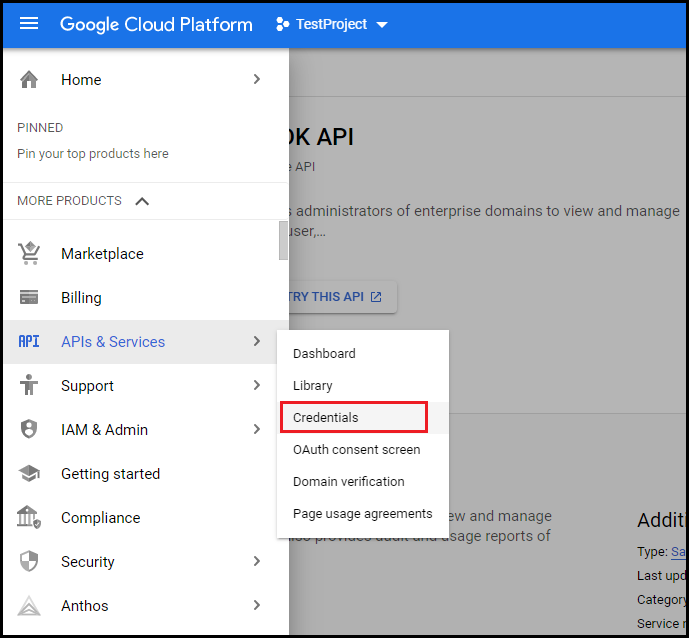
Click Configure consent screen.
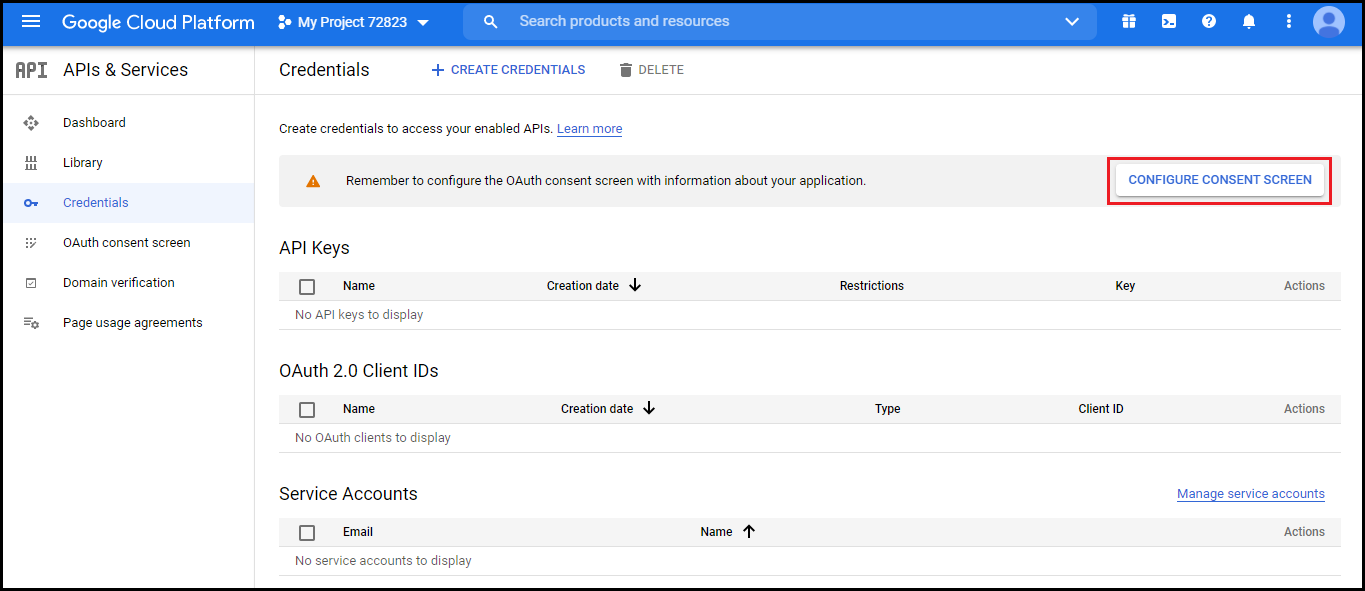
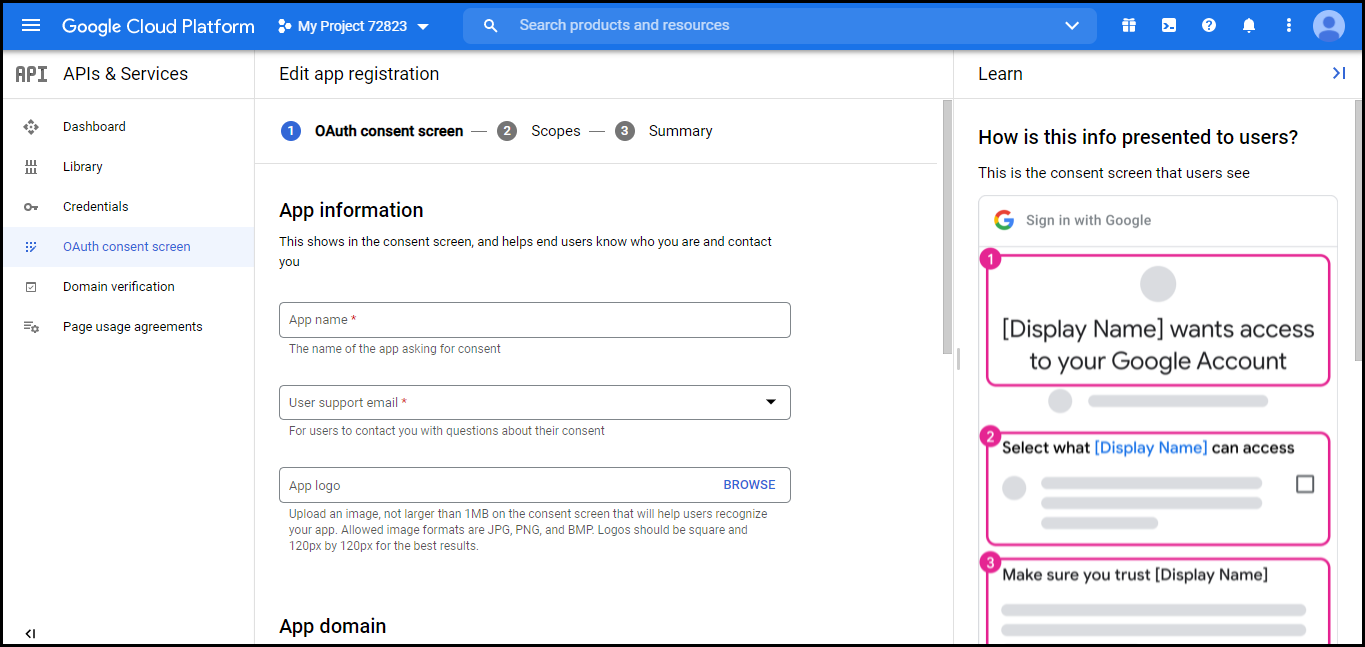
- In the OAuth consent screen section, fill all the required information and click Save And Continue. (Keep the App Domain and Authorized domains blank).
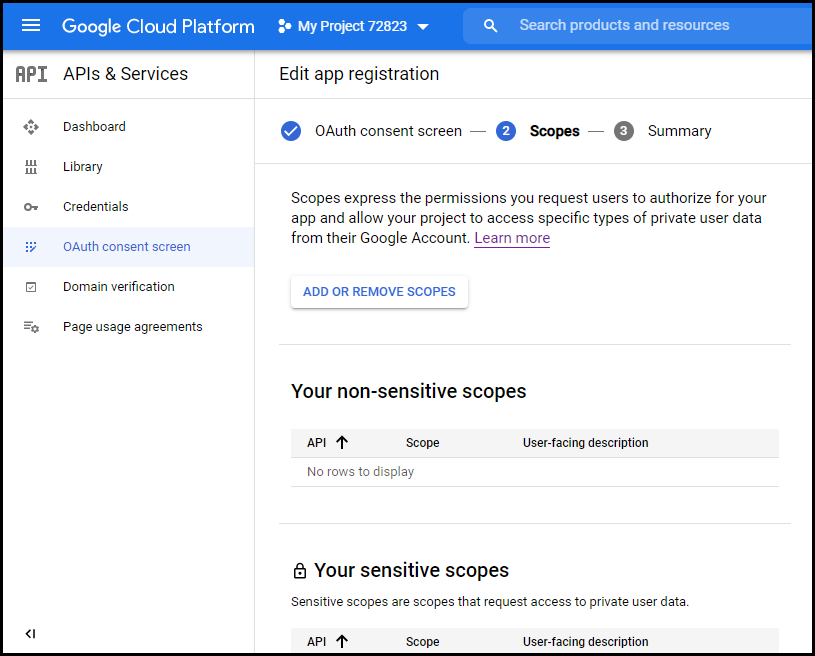
- In the Scope section, keep everything blank and Click Save And Continue.
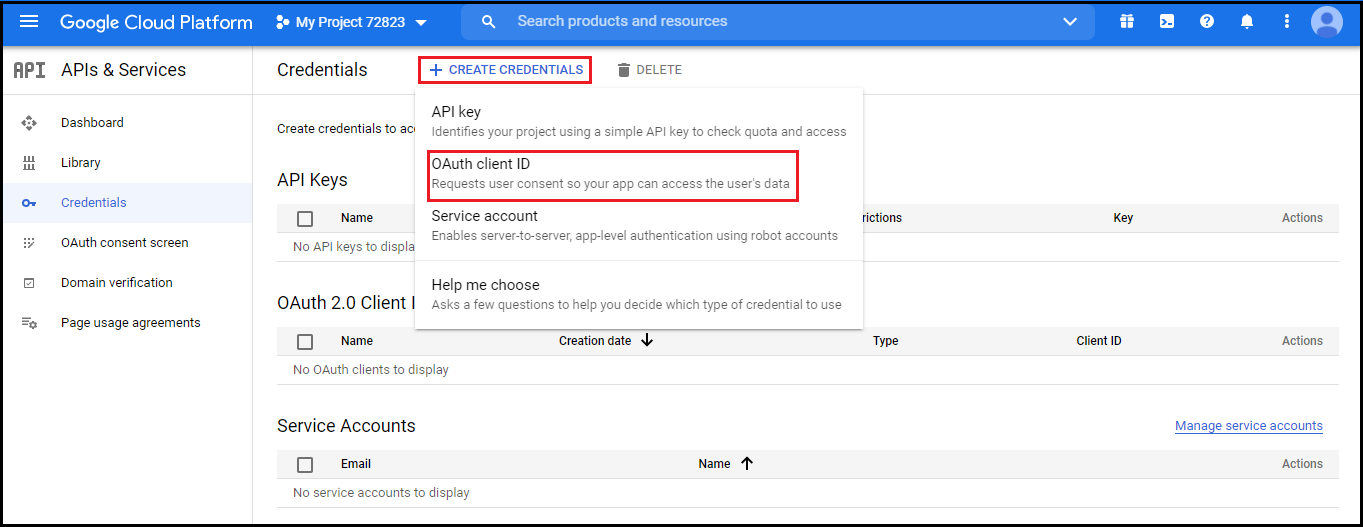
- Check summary and navigate to Credentials in left pane. Click Create credentials. Select OAuth client ID.
- Select Web Application in Application Type dropdown. Enter application name and add below URL in Authorized redirect URIs and click Create.
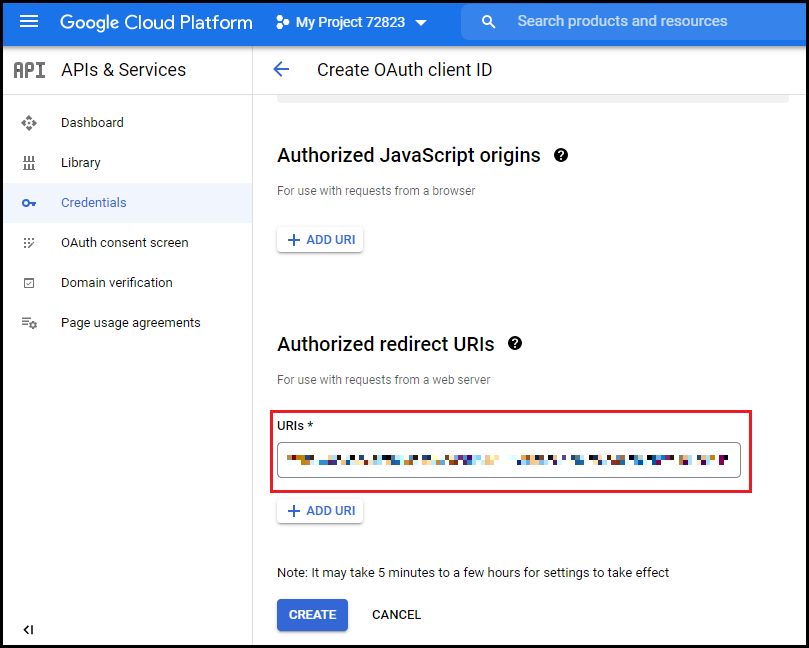
https://cnsdev.qhtpl.com/cns/
/webcns/idp-management/add-edit-idp
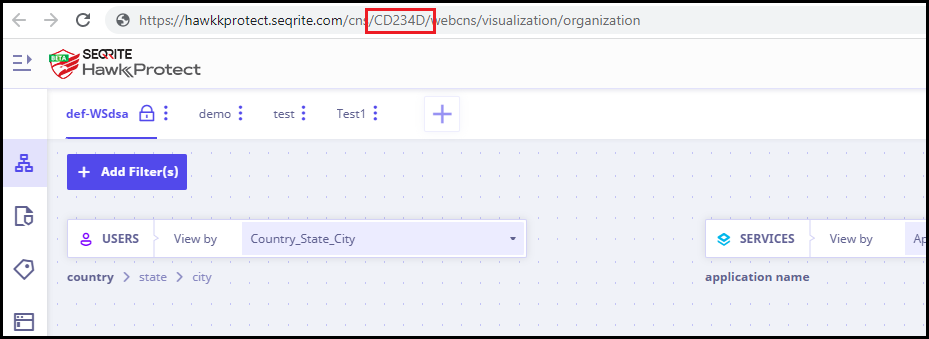
https://cnsqa.qhtpl.com/cns//webcns/idp-management/add-edit-idp Note:
Replacewith your tenant code. You will get tenant code in your admin console URL. Refer the following image.
- Copy Client ID and Client Secret. Download JSON to get Project ID.
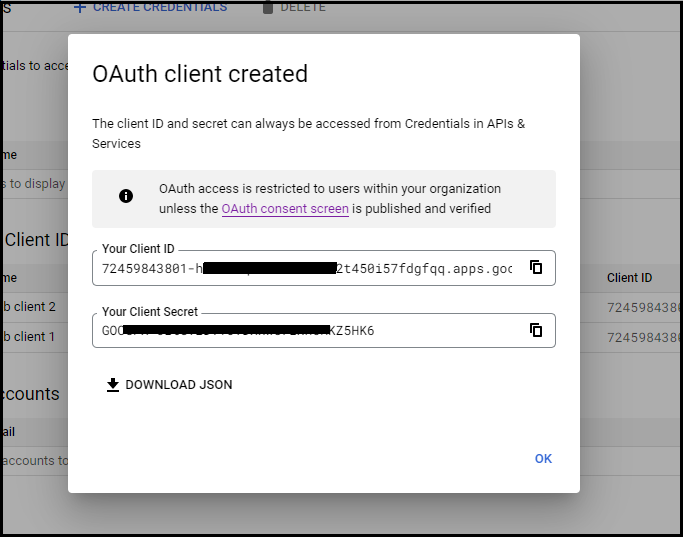
Use Client ID, Client Secret and Project ID to configure Google Workspace IDP in Hawkk Protect Admin Console.
Reauthorization workflow
Removing existing OAuth client ID from google cloud console
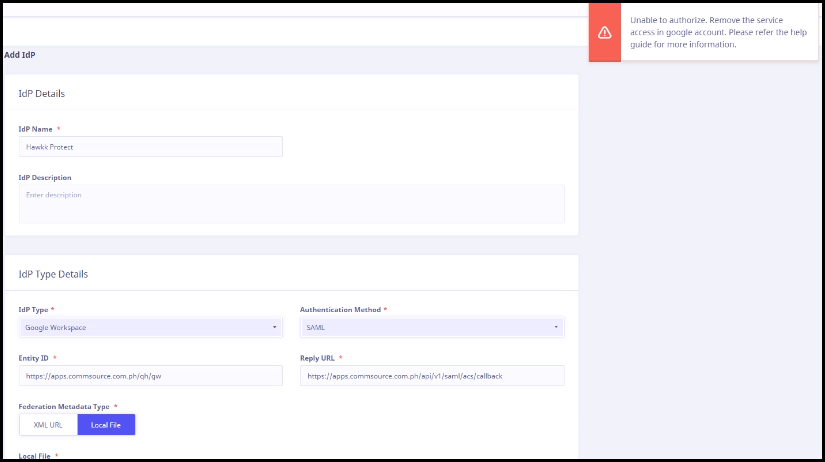
If the OAuth client ID has been authorized and already in use, then an error occurs on the Add IdP page for IdP type Google workspace.
We need to remove this OAuth client ID from google cloud account permissions page (URL).
To remove the existing OAuth client ID from google cloud console permissions page, follow these steps.
- Navigate to permissions page (https://myaccount.google.com/permissions) on google cloud console.
Note:
The admin user must be logged in for accessing this page.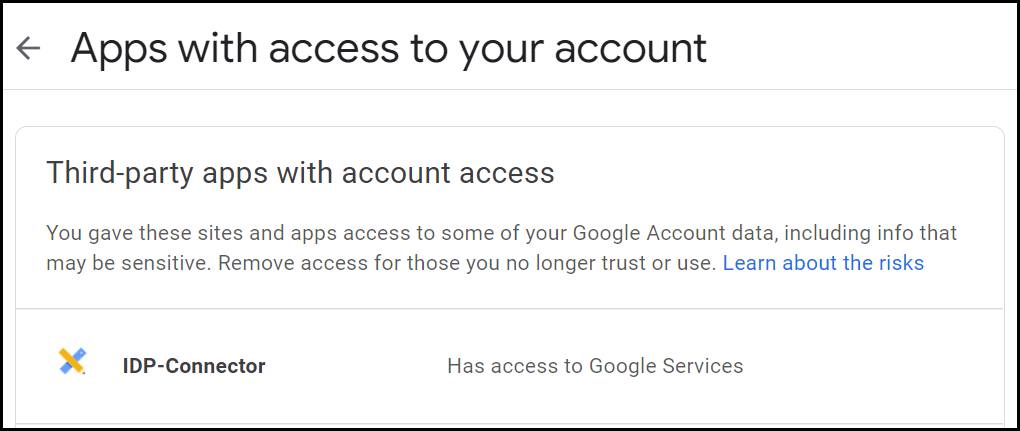
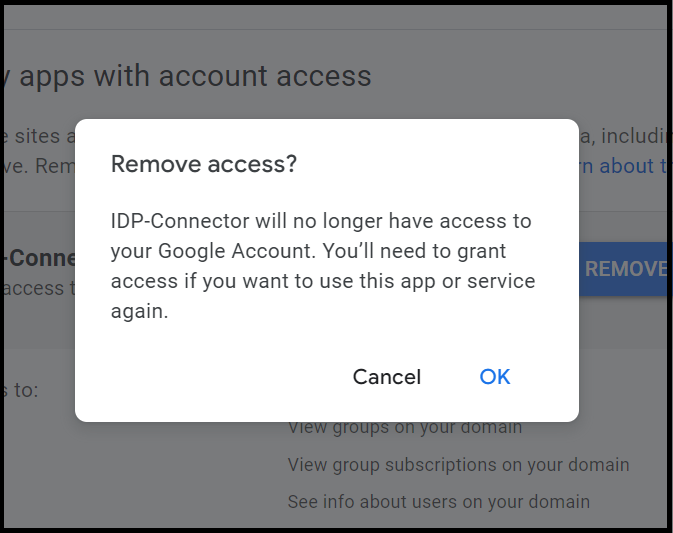
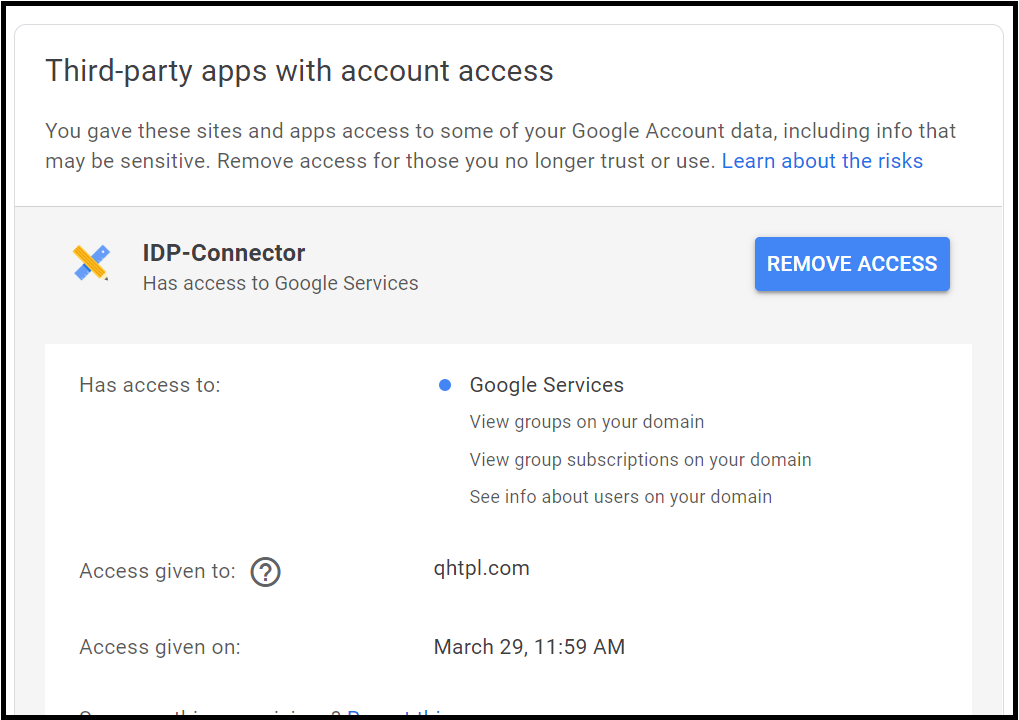
- Click the OAuth client ID for which you want to remove the access and click Remove Access.
- Click OK.
- Now you can add this OAuth client ID on the Add IdP page.